Hi All,
in this article I’ll show you how to setup ARR as a Reverse Proxy for Lync / Skype for Business / Office Web App / Office Online Server (and if you want for Exchange, SharePoint, ADFS…..) and, more important, how to use a very simple but useful trick to publish many lyncdiscover. with a simple 5 Domains SAN Certificate or a Wildcard certificate.
Scenario
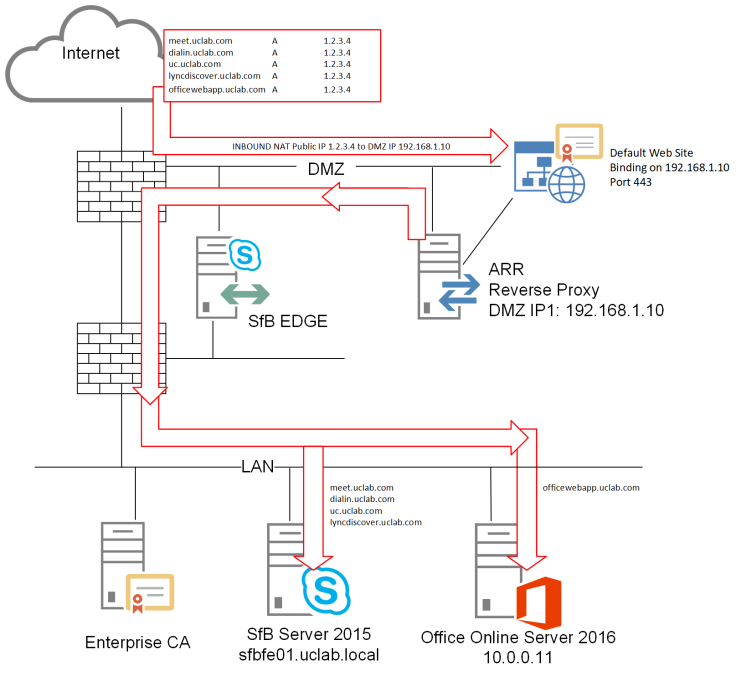
Let’s assume that you have the following public DNS A Records for your SfB deployment:
| Record | Type | Value | Note |
| meet.uclab.com | A | 1.2.3.4 | Meet Simple URL Only 1 for deployment |
| dialin.uclab.com | A | 1.2.3.4 | Dialin Simple URL Only 1 for deployment |
| uc.uclab.com | A | 1.2.3.4 | External Web Service URL 1 for each Front-End Pool |
| lyncdiscover.uclab.com | A | 1.2.3.4 | lyncdiscover. 1 for each SIP Domain |
| officewebapp.uclab.com | A | 1.2.3.4 | Office Web App URL normally 1 for deployment |
- The Public IP is 1.2.3.4 and there is a NAT to 192.168.1.10
- Only HTTPS traffic is allowed.
- On ARR we will use a SAN (5 domains) or Wildcard SSL Certificate from a Public CA (Digicert for example).
Step 1: ARR Setup
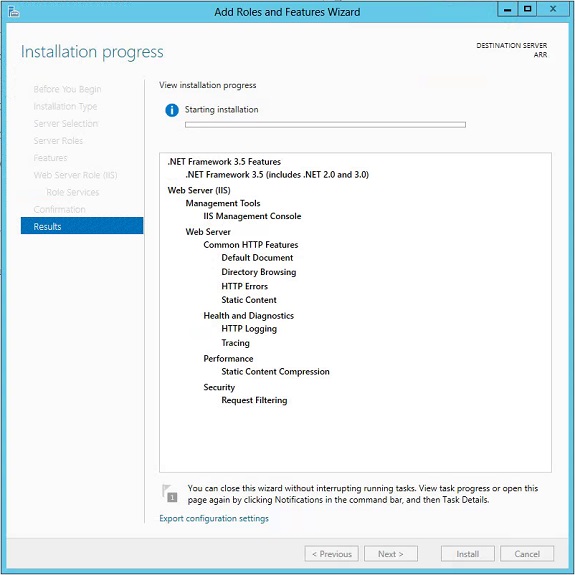
On a Windows Server 2012 R2 or 2016 server install:
- .NET Framework 3.5
- IIS with following components
- Download Microsoft Web Platform Installer http://www.microsoft.com/web/downloads/platform.aspx and install it
- Search ARR and install Application Routing Request 3.0
- Install in the Certificate Store the CA Chain of the internal PKI
Step 2: ARR Customization
Set the Worker Process to Always Run:
- Launch IIS Manager
- Select Application Pools (by default, DefaultAppPool is the corresponding application pool for the Default Web Site)
- Right-click on DefaultAppPool in the right-hand side and then click on Advanced Settings: change the Idle Time-out (minutes) value from 20 to 0 (zero) to disable the setting and then click OK to save the changes
- Right-click on DefaultAppPool in the right-hand side and then click on Recycling: clear the Regular time intervals (in minutes) checkbox so that it is blank
- Under the IIS root, open Request Filtering.
- Click Edit Feature settings on the right and change the Maximum allowed content length to 2147483648 (this is mandatory for Exchange Publishing)
Step 3: ARR Network Settings
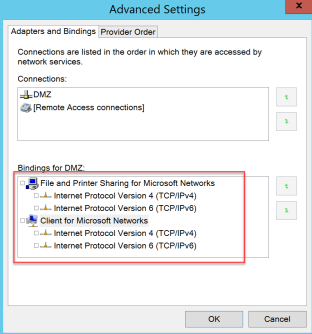
In our example ARR NIC is configured with a DMZ IP 192.168.1.10.
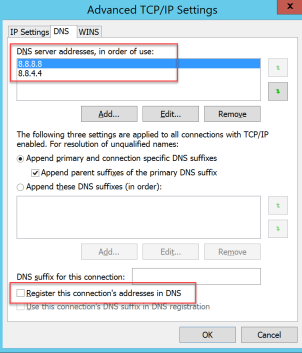
For improved security it is recommended to use external DNS + hosts file and to remove bindings on “File and Printer Sharing” and “Client for Microsoft Networks”

Step 4: obtain Public SSL Certificate and use it on ARR
To create CSR I always suggest to use DigiCert Certificate Utility for Windows (https://www.digicert.com/util/).
Follow instructions on this page CSR Creation Instructions for Microsoft Servers https://www.digicert.com/util/csr-creation-microsoft-servers-using-digicert-utility.htm
Here you can find two examples with a 5 Domains SAN and a Wildcard request.
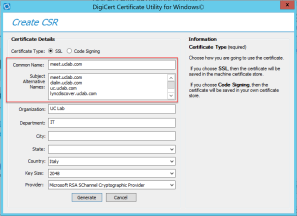
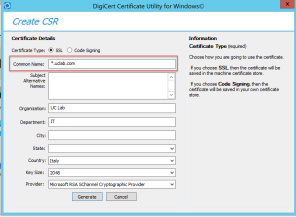
Once you have obtained the public key, load it on the server following on of these instructions:
- https://www.digicert.com/util/ssl-certificate-installation-using-digicert-utility-for-microsoft-servers.htm
- https://www.digicert.com/csr-creation-ssl-installation-iis-10.htm#single-certificate
In this article I will use the SAN certificate
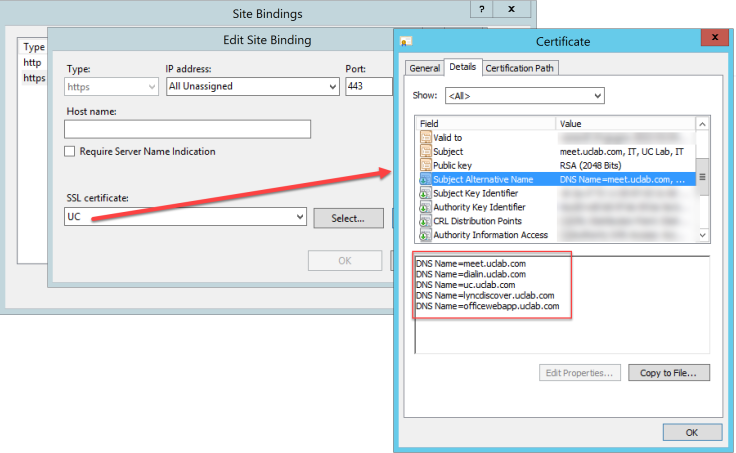
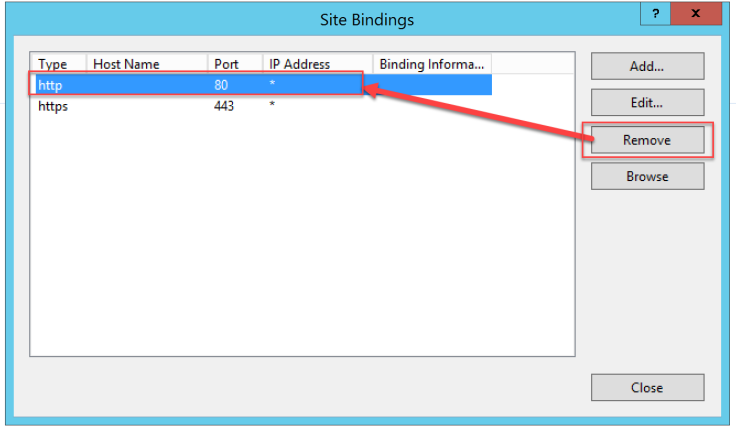
It is better to remove binding on http
Step 5: configure standard SfB and Office Web App Farms
Now that ARR is ready, we can create standard Lync / Skype for Business and Office Web App / Office Online Server Farms.
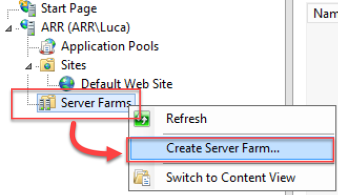
Open IIS Manager -> Server Farms -> Create Server Farm….
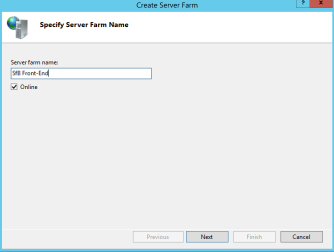
Start with “SfB Front-End”
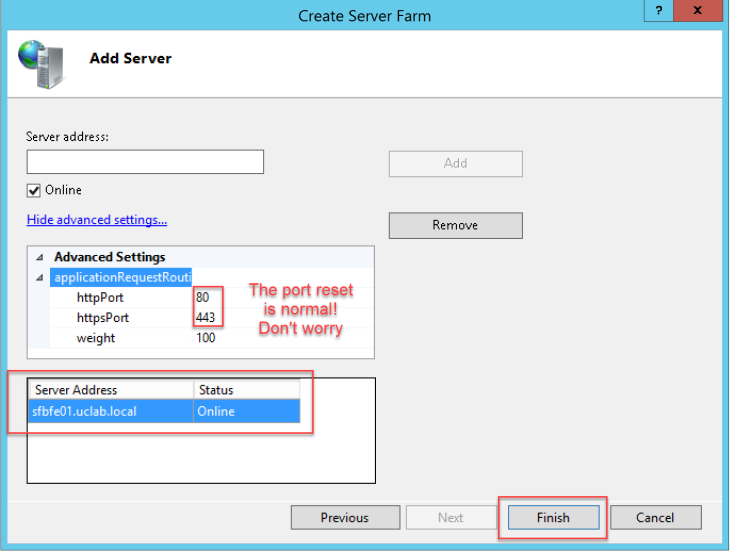
In Server address enter the FQDN of your SfB Front-End Standard Pool.
Be careful to expand Advanced Settings and enter httpPort 8080 and httpsPort 4443 because this traffic needs to go to the External Web Service Virtual Site on the Front-End, then clicc Add
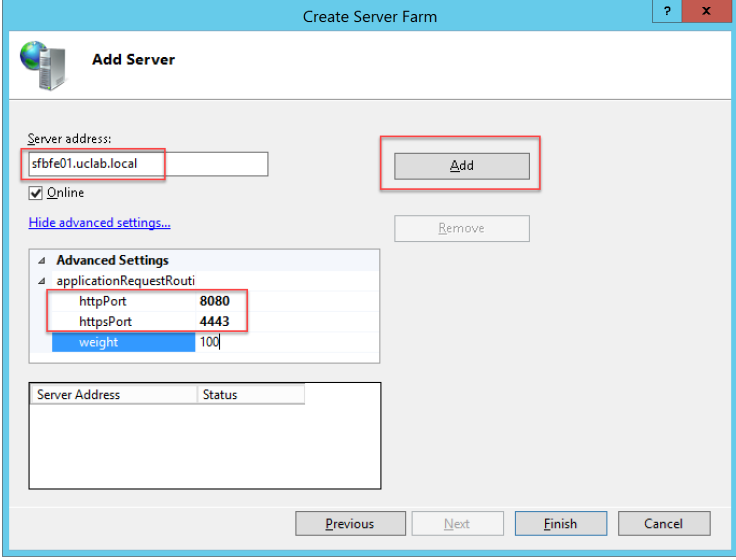
Note: the port reset after you click Add is a normal behaviour, don’t worry about that.
Click Finish.
Remember to add IP and FQDN to the hosts file.
Repeat the process for Office Web App Farm.
Note: you have to use standard ports 80 and 443.
At the end you will have two new Farms, like the image below.
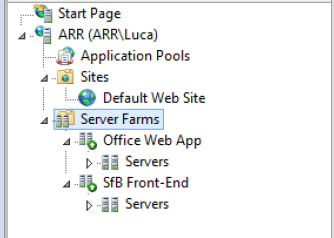
For each Farm, select it and set the Caching and Proxy value as suggested.
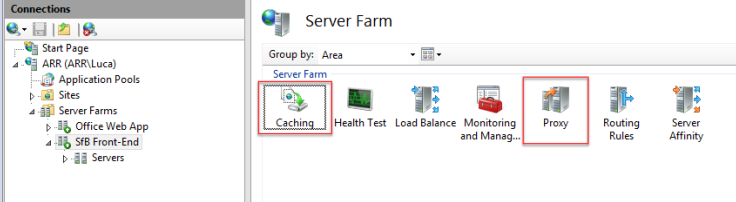
Caching
SfB Front-End Farm: Disable disk cache
Office Web App Farm: Disable disk cache
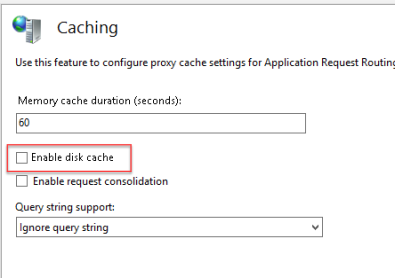
Proxy
SfB Front-End Farm: Time-out to 1200 and Response Buffer Threshold to 0
Office Web App Farm: Time-out to 300 and Response Buffer Threshold to 0
Step 6: configure URL Rewrite Rules
Before we can correctly setup Rewrite Rules, it is important to understand how ARR “think”. Incoming request could be described by these basic components:
{HTTPS}://{HTTP_HOST}/{URL}?{QUERY_STRING}
So an incoming request for
https://meet.uclab.com/Meet?key=A1B2C3D4
correspond to:
{HTTPS} = on
{HTTP_HOST} = meet.uclab.com
{URL} = Meet
{QUERY_STRING} = key=A1B2C3D4
Select the ARR Server itself in the left tree -> URL Rewrite
Double click on the firts rule “ARR_SfB_Front-End_loadbalance”
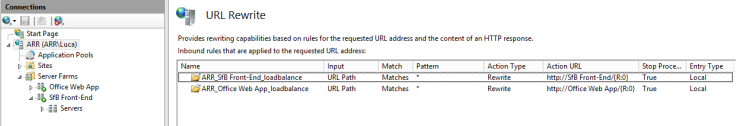
Match URL
Set Regular Expression and (.*) as Pattern
Note: this is not mandatory, you can leave Wildcard and * as the default settings, but I prefer to use RegEx in my rules
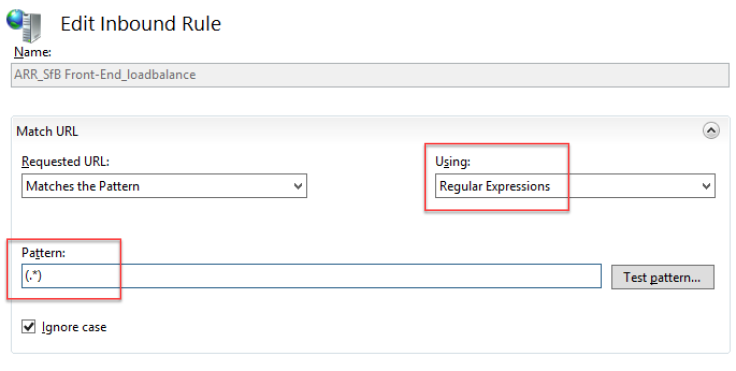
Conditions
Add these two conditions:
{HTTPS} = on
{HTTP_HOST} = (meet|dialin|uc|lyncdiscover).uclab.com
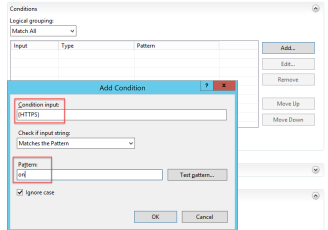
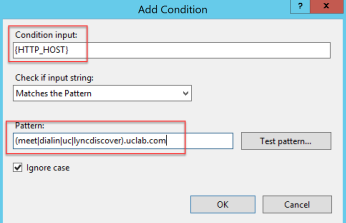
Set Action Scheme on https://
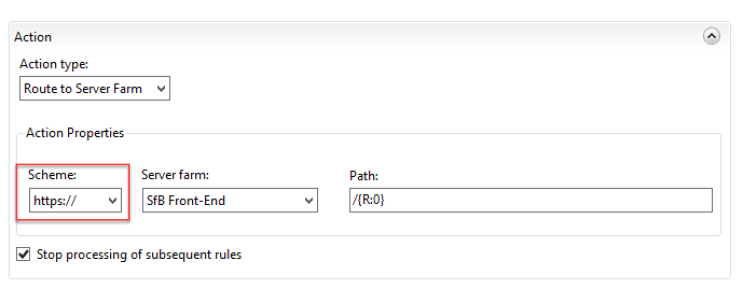
Now open the “ARR_Office Web App_loadbalance”
Repeat same process for Office Web App, with Conditions
{HTTPS} = on
{HTTP_HOST} = officewebapp.uclab.com
Step 7: Reverse Proxy test
Test the Reverse Proxy, trying to open some pages on SfB and Office Web App from Internet, like
https://dialin.uclab.com
https://officewebapp.uclab.com/hosting/discovery
Remember to add your CA Chain to Certificate Store on ARR Server!
Evolution of the scenario: add more SIP domains
Now that everything is working with your Primary SIP domain (uclab.com in this example), your Company/Customer ask you to add other SIP domains to SfB deployment, for example ucdev.net, uc4u.biz, ucme2.it and (many) others.
What you cannot avoid: to buy more “lines” in the SAN certificate used on EDGE server. You NEED one line sip. for each domain plus one for Webconf EDGE Service. Period.
What you CAN avoid: to buy more SAN “lines” for Reverse Proxy SSL certificate!
On your Reverse Proxy, ARR or other brand, you can use existing certificate (SAN or Wildcard) without the need to expand it, you only need a new Public IP.
Let’s see how.
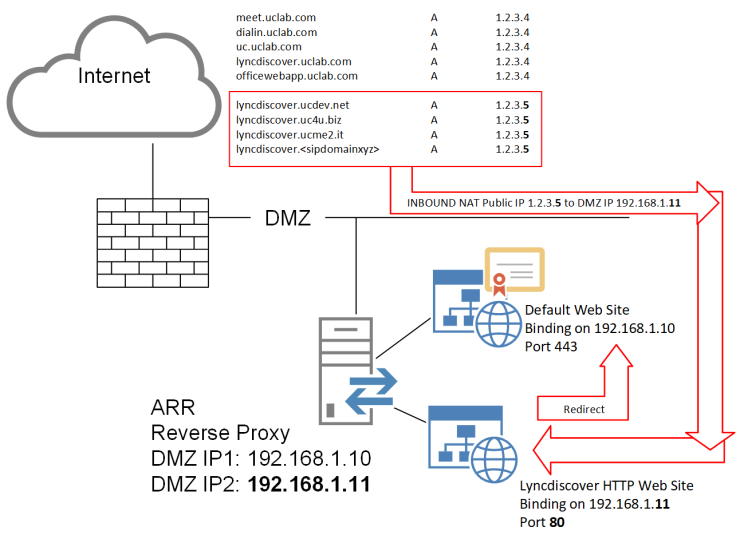
As explained at the beginning of the article, for every SIP domain added to the deployment, the only mandatory Reverse Proxy related FQDN is lyncdiscover.
In this example there is a lyncdiscover.uclab.com (present in certificate), and we have to manage also
lyncdiscover.ucdev.net
lyncdiscover.uc4u.biz
lyncdiscover.ucme2.it
These records are used by clients as primary registration lookup method.
It is important to remember these informations:
A. Protocol and search order:
1. https://lyncdiscoverinternal.SIPDomain 2. http://lyncdiscoverinternal.SIPDomain 3. https://lyncdiscover.SIPDomain 4. http://lyncdiscover.SIPDomain
B. It is possible to redirect SfB PC Client incoming HTTP traffic to a different HTTPS URL
C. It is not possible to redirect SfB Mobile Client incoming HTTP traffic (as explained here https://ucwa.skype.com/documentation/GettingStarted-RootURL)
If you merge these informations, you have the solution for our task:
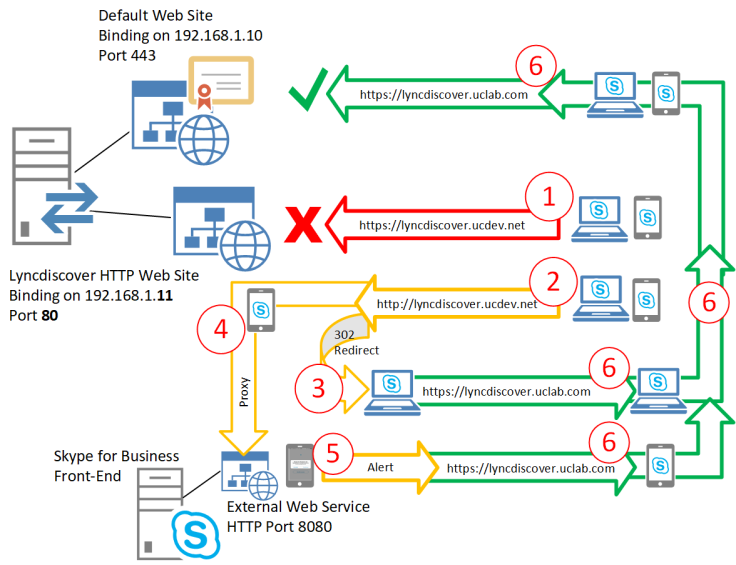
- both clients (PC or not) of ucdev.net will search for https://lyncdiscover.ucdev.net, but Lyncdiscover HTTP Web Site do not listen for HTTPS traffic, so client do not get any answer but not even Certificate mismatch errors.
- Then both clients try to use http://lyncdiscover.ucdev.net
- ARR redirect HTTP traffic from SfB PC Clients to https://lyncdiscover.uclab.com WITHOUT any alert or warning
- ARR proxy HTTP traffic from Mobile Clients to Front-End External Web Server on port 8080
- SfB Mobile Clients get an alert to authorize HTTP Redirect
- both clients access the SfB External Web Service via https correctly
Step 8: configure ARR for lyncdiscover redirect
- Assign a new DMZ IP and a new Public IP to ARR. NAT the Public IP to DMZ IP and allow http traffic only, not https (see example below)
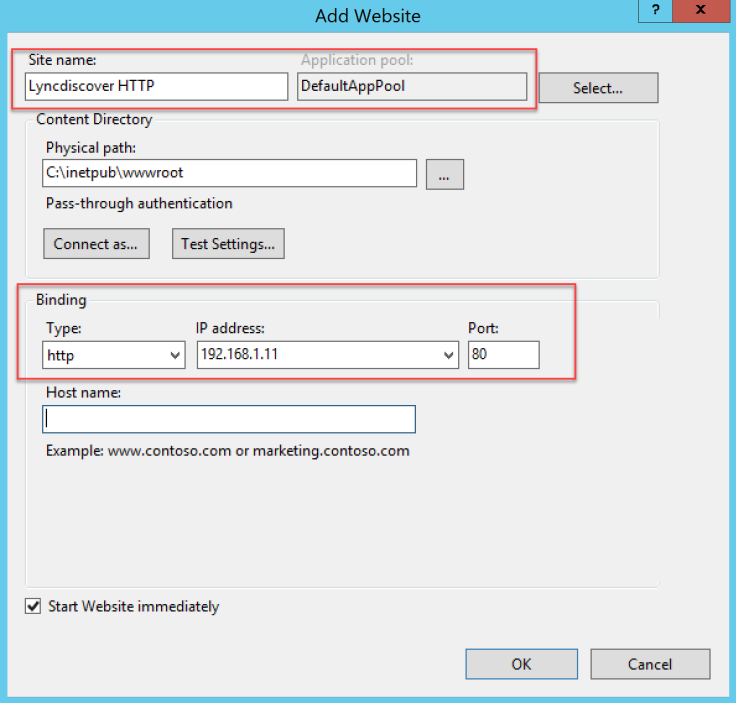
- Add a new Website with these settings (ok, you can change the name if you want) 🙂
- Check the binding on Default Site, be sure it listen the primary IP only
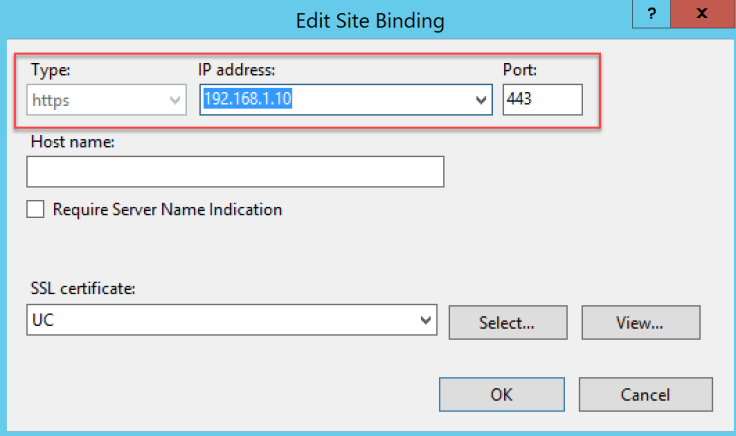
- You will obtain something like this
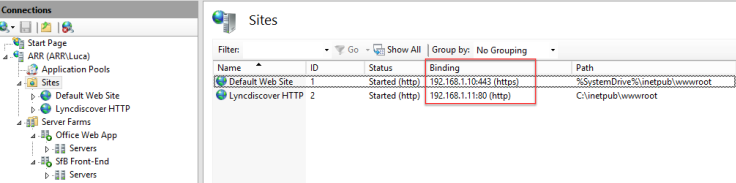
- ARR Root -> URL Rewrite -> Add Rule(s) -> Blank rule -> OK
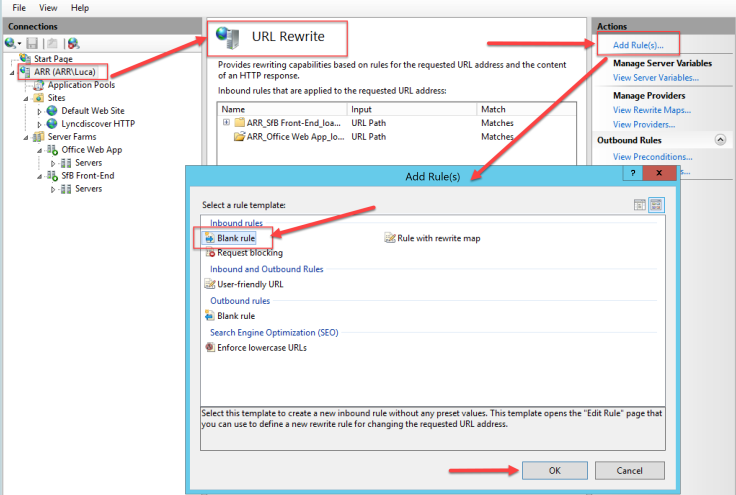
- Configure the new rule as image below
Take care on Conditions
{HTTPS} = off
{HTTP_HOST} = lyncdiscover.(ucdev.net|uc4u.biz|ucme2.it)
you have to replace these additional example SIP domains with yours 🙂
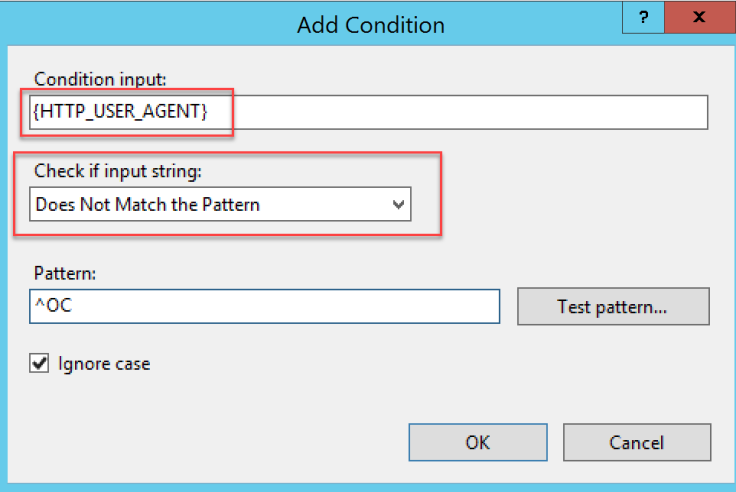
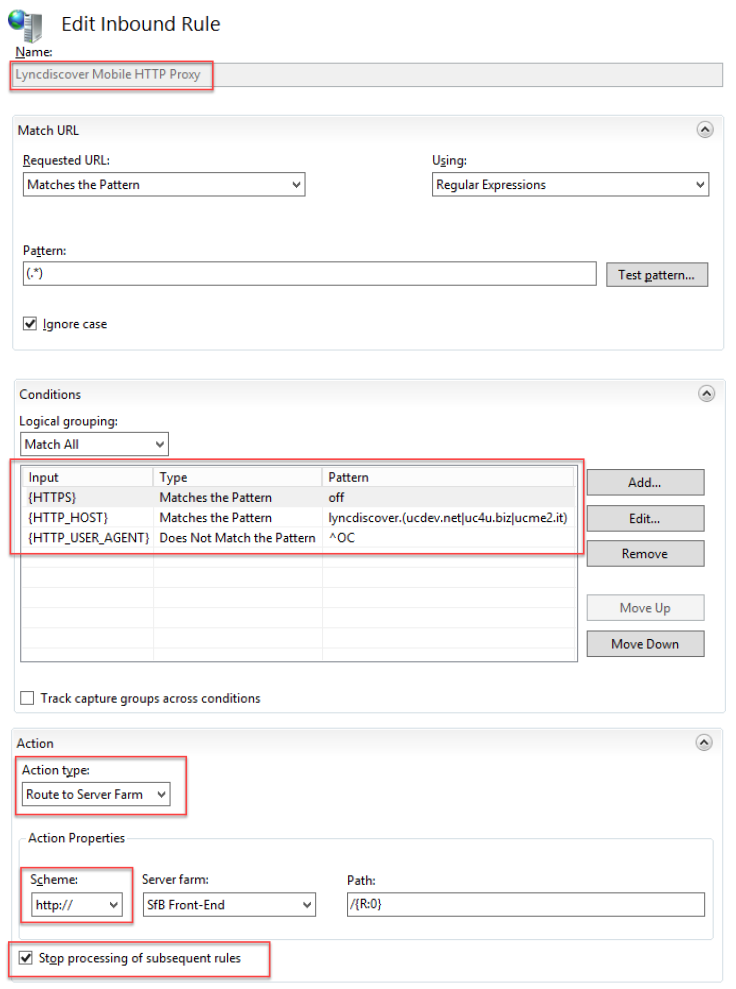
- Repeat point #5 and Create a new blank rule “Lyncdiscover Mobile HTTP Proxy”, this will manage incoming traffic from SfB Mobile Clients
- Configure the new rule as image below
Take care on Conditions
{HTTPS} = off
{HTTP_HOST} = same pattern as previous rule
{HTTP_USER_AGENT} != ^OC
(note: OC is the User Agent of SfB PC Client, so this rule works for everything that is not the SfB PC Client)
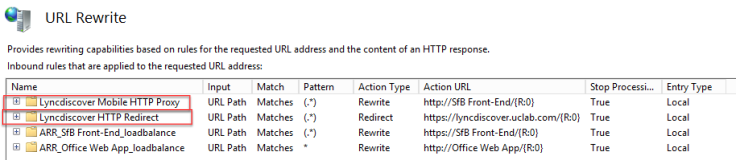
- adjust the priority of rules like image bolow, with Lyncdiscover Mobile HTTP Proxy above Lyncdiscover HTTP Redirect
- Test it and enjoy these simple but useful rules!
As always, I hope this page could help some of you.
Best Regards
Luca
This is a great article, we did a setup strictly following this guideline. It worked perfectly immediately.
LikeLiked by 1 person
This article worked perfectly keep it up.
LikeLiked by 1 person
Thank you Jerson, glad to be helpful
LikeLike
@Luca Vitali,
Nice post man.
You know a way to do the same process above to support federation with external partners, no need to issue new public certificates, examples:
Install a server with IIS and port redirection or new VIP with port redirection or an uncertified VIP.
Exchange has a method for this as links below:
https://marckean.com/2013/07/12/exchange-2010-autodiscover-for-multi-tenant/
https://social.technet.microsoft.com/wiki/contents/articles/5787.exchange-2010-multi-tenant-autodiscover-and-dns-configuration.aspx
https://social.technet.microsoft.com/wiki/contents/articles/6818.exchange-2010-multi-tenant-autodiscover-service.aspx
http://www.azure365pro.com/how-to-create-autodiscoverredirect-record-for-multi-tenant-scenario-in-exchange-2013/
LikeLiked by 1 person
Hi Evandro, thank you.
I’m sorry but I cannot understand what do you meen with “support federation with external partners no need to issue new public certificates”, could you be more clear?
Regards.
Luca
LikeLike
Luca,
On the Lync Server Multitenant Hosting Pack v2 platform
(SW_DVD5_Lync_Server_2013_English_Hosting_Pack_MLF_X19-04580), was supported multiple domains with the hoster domain certificate because it was a retail environment where the federation service with external domains worked for all tenants without having to issue a new certificate for each new domain.
You can configure federation without the need for SAN certificates for AutoConfig and federation.
In this document published at the time, there were scripts that configured the communication of each tenant of the multi-tenancy environment.
(10.2.2 Configuring federation with other Hosting Pack deployments)
Microsoft_Lync_Server_2013_Multitenant_Pack_for_Partner_Hosting_Deployment_Guide.pdf
Param(
[string]$MasterID
)
Import-Module ActiveDirectory
Import-Module LyncOnline
Import-Module Lync
$OU = “OU=$masterID,OU=Provider,OU=hosting,DC=prod,DC=domain,DC=local”
$OUObject = Get-ADOrganizationalUnit -Identity $OU
$GUID = $OUObject.ObjectGUID
$all = New-CsEdgeAllowAllKnownDomains
Set-CsTenantFederationConfiguration -Tenant $GUID -AllowedDomains $all
Invoke-CsManagementStoreReplication
11 Create Tenant DNS Records
Several tenant-specific DNS records are required for tenant users to be able to use hosted Lync Server easily. Lync Server clients comply with SIP RFCs, which state that TLS connections must require that the server’s domain name match the SIP domain name of the client user. The client looks for a service (SRV) record with a matching domain name, which in turn must point to a server or servers with matching domain names.
The following table shows which records need to be created for each SIP domain to be used by a given tenant.
Tenant-specific DNS Records
Type FQDN Target IP address/FQDN Port Maps to/comments
SRV _sip._tls. sip. 443 Used for automatic configuration of the lync client – maps to hosters Access Edge
SRV _sipfederationtls._tcp. sip. 5061 Used for federation with other lync deployments – maps to hosters Access Edge
Can I express a more clear and detailed?
LikeLike
The problem: https://blog.machsol.com/microsoft-skype-for-business/federation-among-tenants-on-hosted-skype-for-business-platform-and-skype-for-business-online
LikeLike
Hi Evandro,
yes now it’s much more clear 🙂
First of all, I’ve never used Hosted Pack, but as expressed by the latest article, SfB Online look for a SAN certificate on the EDGE Access with every sip. listed.
It’s not possible to avoid it with the same method of this article for two reasons:
1. Federation traffic do not pass through ARR but via EDGE Access
2. This method works only because clients look for https AND HTTP, and redirect works only for HTTP. Federation traffic is between servers, works only on port 5061 with SIP/MTLS, no way to avoid it.
I’m sorry.
Best Regards
Luca
LikeLike
Luca,
Thanks anyway.
wish you much success in your professional career.
LikeLike
I wish you much success in your professional career.
LikeLiked by 1 person
Hi Luca,
I’m using IIS ARR :
* for 3 applications (Exchange, office Web App and Skype for business)
* with 2 NIC, 1st to inside the network, secondary for internet with 3 ip for each application
Should I have to use one certificate for all (sfb, exch and owapp) or one certificate per application ?
Can I use the existing certificate of all application ?
Where I have to install application certificate, on internal nic ou external nic ?
Thank you for your answer
LikeLiked by 1 person
Hi Tien,
first of all I suggest to never user 2NIC on ARR, only one in DMZ. It’s more simple and it works like a charm! I’ve never found any reason to use 2 NICs on ARR.
Second: yes, you can publish Exchange, SfB and Office Web App with 1 single Public IP and 1 single Certificate! That’s one of the reason to use a Reverse Proxy, lower costs and simplify deployment.
In that case you have to use a single certificate that contain every fqdn name used by your applications, maybe a Wildcard cert like *.yourdomain.com
Obviously if you need to use the redirect described in this article, you need to have 2 Public IPs on ARR, one for http/https (with a single common certificate) and one with only http to use the redirect.
Let me know.
Regards
Luca
LikeLike
Hi Luca,
Could you give more details about irp setting to allow mobile phone connexion to sfb server ?
Thank you for your reply I will change my setting.
LikeLike
Hi Tien, what’s not clear in the article?
LikeLike
Hi Luca,
I apologize, I understood that you didn’t want to change the existing certificate on you IRP so you configured:
• sfb -> https for the domain uclab.com
• sfb -> http redirect for the domain ucdev.net -> https for the domain uclab.com
If I have only one domain, uclab.com and I already configured https for sfb on pc.
For sfb on mobile phone using the same domain uclab.com, I would like to know if I must configure “lyncdiscover http redirect” or if “lyncdiscover Mobile HTTP Proxy rule” is enough?
Thank you very much
LikeLike
Hi Tien,
if you have only one SIP Domain you do not have to use the http redirect “trick”, you only have to setup the first part of the ARR publishing rule described in this article (from step 1 to step 7).
LikeLike
Hello Luca,
Thank you for the article.
I am currently learning Skype for business and planning to setup a test lab for Skype,exchange and only have one public IP. I want to check if you can guide me here on setting up enterprise voice as well as publishing the resources to outside network for testing etc?
As i have only one public IP can you please let me know the steps need to be followed for a successful deployment?
Appreciate your help here.
Many thanks
Regards,
Pavan
LikeLike
Hello Luca,
Any response here will be greatly appreciated. Thank you
LikeLike
Hi Pavan, if you need to correctly publish Exchange and SfB, you need at least TWO Public IPs, one for ARR and one for SfB EDGE in the Single Public IP with NAT configuration. You can use the same Public IP of ARR to route also SMTP traffic to Exchange with a port forward on your firewall. On your Public DNS you will create the Exchange, SfB and OOS records. On ARR you will need to create 3 Farm (Exchange 2016, SfB 2016, Office Online Server 2016), and 3 simple Rule, one for Exchange, one for SfB and one for OOS to match the differents host names and route the traffic to the correct farm.
Regards. Luca
LikeLike
Thank you very much Luca on coming back to me on this.Much appreciate it! So when i create farm for exchange on ARR i need to include ports 25 and 443 similar to 80&443/8080/4443 for other services and then port forward port 25,80&443 on the firewall? Also i was researching about the federation services which edge service provides and seems needs a microsoft agreement number to make it work. As i am doing a home lab is there anyway to by pass this so that test things etc?
I believe Skype for business 2019 would be the last on perm as ppl were talking that teams might take over things going forward?
Hope to hear from you soon on this.
cheers
LikeLiked by 1 person
Hi Pavan, glad to help you.
First question (firewall): correct
Second question (federation): the only number you need is the Enterprise Agreement to establish Federation with Skype Consumer via this site https://pic.lync.com , maybe you can avoid it 🙂
Federation between SfB servers is “free”, but it works only if you use Trusted Public SSL Certs. You can use Let’s Encrypt Certs for free.
SfB 2019 is not updated at this moment, I suggest to use the old but frequently updated SfB 2015.
Agree, SfB is reaching the End, start to use Teams as soon as possible.
Regards
Luca
LikeLike
Hello Luca,
Good article!! but i have a problem ;(
I have 3 Sip, one prinpipal sip domain (domain1) and two secondary sip domain (domain2 and domain3)
When you use the tool Microsoft remote connectivity Analyzer with domain2 or domain3 show the error the port is not open (443), but i dont understand why the tool only search https://lyncdiscover.domain2.com and dont search http://lyncdiscover.domain2.com, so the redirect not working, but if you test the url http://lyncdiscover.domain2.com internaly redirect correctly to https://lyncdiscover.domain1.com
Can you help me?
Regards
LikeLike
Hi Koke, I’ve not understand if only the Remote Connectivity Analyzer give you an error or if you cannot connect with domain2 and 3 at all. In the first case, simply do not care. In the second case, there is something in your configuration that do not work correctly, check it again please.
Best. Luca
LikeLike
Hello, thanks for your fast answer.
i cannot connect with domain2 and 3 at all, i´m going to explain the scenario:
i have 3 server for sfb 2015:
– 1 Edge server
– 1 Front server
– 1 ARR server (server configure with this great article)
I have 3 server with Exchange 2013 with DAG
When one user connect to Skype or exchange with domain1 work correctly internal and External (for the moment i havent changed the public DNS to redirect to ARR Server, now redirect to as this:
sip.domain1.com => redirect Front end server of sfb 2015
av.domain1.com =>redirect edge server of sfb 2015
meet.domain1.com =>redirect edge server of sfb 2015
dialin.domain1.com =>redirect edge server of sfb 2015
lyncdiscover.domain1.com =>redirect edge server of sfb 2015
lync.domain1.com =>redirect edge server of sfb 2015
I want sure that ARR Server work correctly with domain2 and 3 before to change domain1 in the public DNS.
When one user connect to Skype with domain1 but with domain2 in Exchange, the Exchange work correctly and the Skype connect correctly but dont see the list of last calls, etc because the domain of Skype and Exchange arent same, for those i want to use your great article to connect skype with domain2 and Exchange with domain2 in the same servers of sfb and Exchange to domain1
Do you understand me?
Sorry for my english
Koke
LikeLike
I Koke, I see many errors in your current configuration. If I can give a hint, try to achieve a perfectly running SfB Deployment with only one SIP Domain, then add the others using my article.
Try to use one of the many articles to correctly configure and publish SfB, your config is not correct at all (sorry). Best. Luca
LikeLike
Hi Luca, I followed your guide and I managed to publish skype4b, the problem that mobile applications don’t work, can you give me some advice?
Thanks Alessandro
LikeLike
Hi Alessandro, if you have issue event with the main SIP Domain, then you have to check again your ARR configuration. This solution is 100% tested and working. If you have issue with secondary SIP domains only, check the second virtual site in http only.
Best. Luca
LikeLike
Hi Luca , sorry I explained myself badly , for the first domain is all ok , the second domain I can not understand if I have to configure in the dns only the lncydiscovery record or even the sip , meet , etc. If I see them configure where I have to direct them
LikeLike
Hi Alessandro, it’s all described in the article, even DNS records. Read it carefully 😉. Best. Luca
LikeLike
Hi Luca, I carefully read your beautiful article, but unfortunately there is something that does not work. I ran the tests of testconnectivity.microsoft.com and in the first test it tells me that the SRV and A records are missing 😦 and in the second test I continue the search on port 443 (Testing TCP port 443 on host lyncdiscover.domain2.it to ensure it’s listening and open) .
Thanks Alessandro
LikeLike
Hi Alessandro, this article explain how to manage HTTP/S related SfB services, so it’s about only to records like lyncdiscover, meet, dialnin and External Web Service URLs.
In that part of the article “Evolution of the scenario: add more SIP domains” you will find information related to how to manage additional lyncdiscover records for yours secondary SIP Domains.
Others records like SRV and EDGE related service are not managed in this article. To answer to your question: you have to creare the whole set of SRV records and sip. records for every single SIP Domains, there is no way to avoid it.
Best. Luca
LikeLike
HI Luca
I thank you for your article, but I think I am forced to renounce the project to help a non-profit association for the covid-19, because I can’t solve the 443 to 80 redirect problem.
1. https://lyncdiscoverinternal.SIPDomain
2. http://lyncdiscoverinternal.SIPDomain
3. https://lyncdiscover.SIPDomain
4. http://lyncdiscover.SIPDomain
always on port 443 of the second domain, requests are sent. If you want you have some tips for a non-profit end, I remain at your disposal
Best Alessandro
LikeLike
Hi Alessandro. The non-profit Association could use M365 licenses that MS offer for free to ONLUS, with Teams and other services. Teams today is far far better than SfB in every aspects, so you do not have to struggle with SfB, this is my tip 🙂
To answer to your question, if you do not have a different IP for the HTTP listener, you have to use the “standard solution” that is “to buy a SAN certificate with every lyncdiscover.sipdomain1.com, lyncdiscover.sipdomain2.com” and so on.
Best. Luca
LikeLike